VPN Encryption Explained: What Most People Still Get Wrong
- Oct 5
- 8 min read

Ever wonder how your data stays private when you’re on airport Wi-Fi, or if it even is private at all? You’re not alone. In a world full of trackers, snoops, and silent data leaks, privacy feels more fragile than ever.
VPN encryption is the process of converting your internet data into unreadable code while it travels between your device and a VPN server, ensuring that hackers, ISPs, or surveillance systems can't see what you're doing online.
This isn’t just a tech buzzword, it’s the core engine behind how VPNs protect your privacy. Without strong encryption, a VPN is just a fancy reroute button. Understanding how it works isn’t just helpful, it’s essential if you care about keeping your information safe in a connected world.
What Exactly Is VPN Encryption and Why Should You Care?
In simple terms, encryption is the process of scrambling your readable data into unreadable code. Think of it like converting a postcard into a locked briefcase.
Anyone who intercepts that briefcase can see you’re sending something, but they won’t have the key to open it. That’s what VPN encryption does with your internet traffic.
What a VPN Keeps Hidden From Hackers, ISPs, and Snoops
When you connect to a VPN, the encryption system kicks in to make sure no one, your internet service provider (ISP), public Wi-Fi snoopers, or even government surveillance agencies, can see what you’re doing online.
The goal is privacy, plain and simple. Not just “hide my IP” privacy, but full-on, scramble-everything-I-send kind of protection.
It’s Not Just Privacy, It’s Data Control, Too
But back to encryption, it’s not just about keeping things hidden. It’s about controlling what happens to your data in transit. VPN encryption ensures no one tampers with your files, redirects your traffic, or injects malicious content midstream.
It’s a shield, yes, but also a seal. It gives you confidence that the data you send arrives untouched, whether it’s a login request, a file transfer, or an app pinging its server. You’re not just unseen, you’re untampered with.
How VPN Encryption Works, Like a Tunnel for Your Data
Imagine you’re sending a postcard (again), no envelope, just your personal messages, URLs, and app activity, right out in the open.
Anyone in the network path, your ISP, hackers on public Wi-Fi, even data-hungry advertisers, can peek. That’s how raw, unprotected internet traffic behaves.
With VPN: Your Private Tunnel Kicks In
Now comes the cloak-and-dagger part. Here’s what happens when VPN encryption kicks in:

Step 1: Your VPN App Scrambles Your Data
Your VPN app encrypts your outgoing data, turning readable info into ciphertext.
Step 2: Your Traffic Enters a Secure Tunnel
The encrypted data travels through a secure tunnel, like driving in a bulletproof tube from your house to a guarded gate.
Step 3: The VPN Server Unlocks It
The VPN server decrypts it and forwards it to its final destination (a website, app server, etc.).
Step 4: The Reply Gets Re-Encrypted for the Trip Back
The response from that site is encrypted again on its way back to you.
From Your Screen, Everything Looks Normal, But It’s Not
From your end, it looks like nothing changed. Websites still load, videos still stream. But underneath? Every click, tap, and scroll is wrapped in encryption like a sealed container in a high-security truck.
That’s the magic of encrypted VPN connections. And once you’ve seen what unprotected traffic looks like (hello, packet sniffers), you’ll never want to go back.
What Types of Encryption Do VPNs Use Behind the Scenes?
Not all encryption is created equal. In fact, how a VPN encrypts data depends on the type of encryption in play and the key system behind it.

Symmetric Encryption: One Key, Fast Speed
This one’s old-school, but still powerful. It uses a single key to both encrypt and decrypt your data. Think of it like a hotel room where both you and the staff use the same keycard. Fast and efficient, but if someone copies that key, you're in trouble.
AES-256, the gold standard in VPN encryption, falls under this category. It’s used by militaries, banks, and yep, most major VPN services.
AES-256 has 2⁵⁶ possible key combinations. That’s a number so huge, even the world’s fastest supercomputer would take longer than the age of the universe to crack it.
What Does 2⁵⁶ Mean
2⁵⁶ means "2 to the power of 256". That's the total number of possible encryption keys AES-256 can generate.
To put it in perspective, that’s:
2⁵⁶ =115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457
That’s more than 78 digits long. Even if a supercomputer tried a billion billion guesses every second, it would still take longer than the age of the universe to crack a single key by brute force.
This is what makes AES-256 virtually unbreakable and why it's trusted by governments, militaries, and top-tier VPNs around the world.
Asymmetric Encryption: Two Keys, Smarter Security
Now this one’s clever. It uses two keys: a public key (to encrypt) and a private key (to decrypt). You can share the public key freely, but only the matching private key can unlock the message. This is great for setting up secure channels, like during the VPN handshake phase.
RSA encryption is the classic here. It’s slower than symmetric options, so it’s usually just used at the start, to exchange keys securely, before switching to something like AES for the actual data.
What’s ChaCha20? A Speedy Alternative for Mobile VPNs
For mobile users or low-power devices, ChaCha20 is rising fast. It’s a symmetric cipher known for being lightning-fast without sacrificing much security. You’ll see it in VPNs that prioritize speed and battery life, like on Android and iOS apps.
Different VPNs use different combos, but good ones are transparent about what they offer. If your provider’s just throwing around buzzwords without naming actual algorithms? That’s a red flag.
What VPN Encryption Really Protects and What It Doesn’t
Now, what exactly does VPN encryption shield once it’s running? The short answer: more than most people realize, but not everything.

Here’s What Your VPN Encryption Actually Hides
Your IP address
Replaced by the VPN server’s IP, making you harder to track.
Your browsing history
Encrypted and invisible to your ISP or network admin.
DNS requests
So outsiders can’t see the websites you’re visiting.
App usage data
Especially useful for messaging apps or video platforms.
Login credentials, emails, and chats
Unless the app itself is unencrypted.
But Wait, Here’s What It Can’t Protect You From
But don’t get too comfortable just yet. VPNs aren’t magic shields. VPN data protection is strong, but it doesn’t block everything.
If you click a malicious link, get phished, or download malware, encryption won’t save you from that. It’ll just deliver the danger... securely.
Why Encryption Alone Isn’t Enough for Real Safety
That’s why VPNs work best with other tools, like antivirus software, password managers, and a healthy dose of skepticism. Encryption protects your traffic, not your decisions.
How VPNs Secure the Connection: Handshakes and Protocols
Here’s where things get technical, but don’t worry, we’ll keep it human.
Before a VPN tunnel forms, there’s a brief digital handshake. No, not the “nice to meet you” kind, but a cryptographic exchange that agrees on the rules: which encryption to use, how to swap keys, and how to keep the channel private.
This step happens every time you connect to a VPN. The stronger and more secure the handshake, the safer your encrypted VPN connection will be.
Then Come the Protocols, The Brains Behind the Tunnel
You’ll often hear about VPN protocols in this context. They’re the frameworks that manage encryption, handshakes, and data flow. Here are a few you’ll see in the wild:

OpenVPN - Reliable, open-source, widely used. Supports strong encryption like AES-256.
WireGuard - Modern, lightweight, fast. Uses ChaCha20 for speed and battery-friendliness.
IKEv2/IPSec - Especially good for mobile devices and network switching.
Each protocol has its pros and trade-offs. The protocol you choose affects how VPN encryption works in practice, how secure, fast, and stable your connection is.
When VPN Encryption Fails And What Could Go Terribly Wrong
So what if that protective layer cracks? When VPN encryption fails, or worse, isn’t even properly set up, you’re no longer in stealth mode. Your traffic might leak out unencrypted, exposing your IP address, DNS queries, or even entire sessions.

The Ugly Truth: What Happens When Encryption Breaks
VPN leaks - These occur when your VPN fails to properly mask your IP or DNS requests. It’s like using a tinted window that suddenly turns clear.
Weak cipher suites - If a VPN uses outdated algorithms (like PPTP or 128-bit RC4), it’s much easier for attackers to brute-force your traffic.
Downgrade attacks - Hackers trick your device into accepting a weaker encryption standard during the handshake. From there, breaking in becomes child’s play.
Shady VPN providers - Especially free ones. Some offer little to no encryption and may even log or sell your data. If your VPN’s free, you might be the product.
This is why transparency matters. If your provider won’t clearly state what encryption it uses, or it hides behind vague claims like “military-grade security” without the receipts, run.
Why Strong VPN Encryption Isn’t Optional Anymore
Not all VPN encryption is built the same. You’ve probably seen terms like “128-bit” and “256-bit” floating around in marketing blurbs, but what do they really mean?
The Math Behind It: What 256-Bit Encryption Really Means
It comes down to brute-force resistance. That is, how hard it is for someone to guess or crack your encryption key through trial and error.
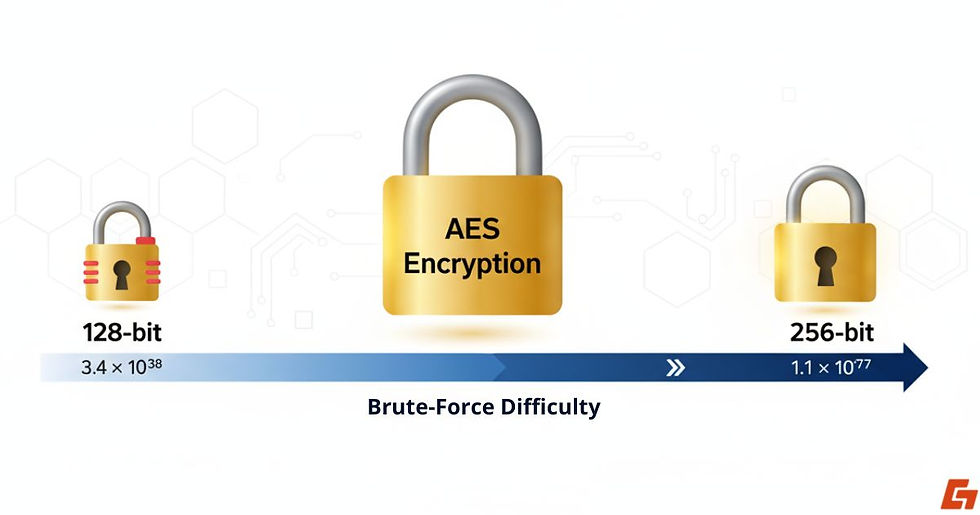
How 128-bit Compares to 256-bit Encryption
128-bit encryption: ~3.4 x 10³⁸ possible combinations
256-bit encryption: ~1.1 x 10⁷⁷ combinations
In other words, even the most powerful supercomputer would need billions of years to crack AES-256.
Stronger Encryption Can Slow You Down, Here’s Why
Stronger encryption comes with a trade-off, performance. The heavier the encryption, the more processing power it takes. That can slow down your connection, especially on older devices or sluggish networks.
Finding Your Fit: Security vs Speed in VPN Encryption
Some VPN providers give you options: speed-first protocols for streaming, and high-security modes for sensitive activity. The best services strike a balance that fits your needs, privacy, speed, or both.
Compliance Demands It: When 256-Bit Is a Must-Have
And if you’re using a VPN at work or in regulated industries (finance, healthcare, legal), strong encryption isn’t just smart, it’s often required by compliance standards.
Is Your VPN Really Encrypted? Here’s How to Know for Sure
Let’s be honest, just because a VPN claims to be secure doesn’t mean it actually is. Want to know if your VPN encryption is doing its job? Here’s how to find out:
1. Use online tools
Sites like dnsleaktest.com, ipleak.net, or browser fingerprinting testers can show if your traffic is leaking outside the tunnel. If your real IP shows up? Red flag.
2. Check the app settings
Most quality VPNs let you see which protocol you’re using, OpenVPN, WireGuard, IKEv2 and what kind of encryption is active (like AES-256 or ChaCha20). If it doesn’t say? That’s not a good sign.
3. Look for transparency
Good VPN providers clearly explain their tech. They’ll mention encryption standards, protocols, and even have third-party audits. Bad ones just shout “secure!” without any proof.
If you see vague terms like “bank-level security” or “anonymous VPN tunnel” but no mention of actual encryption types, you might be trusting a lock with no keyhole.
Why VPN Encryption Is Your Online Safety Net
From scrambled data to secure tunnels, we’ve unpacked the mechanics, types, and real-world impact of VPN encryption and why not all encryption is created equal.
It’s more than just a tech feature; it’s the backbone of online privacy, shielding your activity from prying eyes every time you connect.
So now that you know what’s under the hood, are you using a VPN that actually encrypts your data properly, or just one that says it does?



Comments