Deep Packet Inspection: What It Is and How VPNs Stop It
- 4 days ago
- 9 min read

Ever feel like your internet knows too much about you? It’s not just paranoia, your traffic might be getting scanned, sorted, and throttled without you even knowing.
Deep packet inspection is a method of analyzing internet traffic that goes beyond basic headers to inspect the actual data (payload) within network packets. It's used to monitor, censor, throttle, or block specific types of online activity.
As governments tighten control and ISPs shape what you see, understanding deep packet inspection is essential. From privacy to censorship to smooth streaming, this is the tech standing in your way and VPNs are among the few tools that fight back.
What You Will Learn in This Article
What’s Hiding in Your Internet Traffic? Meet Deep Packet Inspection
Let’s clear up a common misconception first: most internet traffic isn’t just “seen” in terms of where it’s going. With deep packet inspection, it’s also about what’s inside those packets.

It’s Not Just Where You Click, It’s What’s Inside the Packet
So, what is deep packet inspection exactly? It’s a technique used by internet providers, firewalls, and even government surveillance systems to peek beyond the basic metadata of your internet traffic.
Unlike regular routers that glance at the header (the “To” and “From” addresses, basically), DPI takes a much deeper look.
DPI Is Like Someone Reading Your Mail
It reads the actual content, like someone opening your mail instead of just reading the envelope.
That means it can detect specific applications like BitTorrent or VPNs, recognize unencrypted text, and even block access based on what it finds inside.
Whether it’s streaming Netflix, browsing Reddit, or logging into your bank, DPI has the potential to see, sort, slow, or stop it. The scary part? Most of the time, you won’t even notice it’s happening.
Who’s Really Watching You Online? Spoiler: It’s Not Just Hackers
If you're wondering who has the time, or the nerve, to scan your internet traffic that closely, the answer is: more parties than you think.

ISPs: Slowing You Down Without Saying Why
Internet service providers often use deep packet inspection to throttle bandwidth. Streaming too much? Using a torrent client? Your ISP might slow you down, not because they’re short on resources, but because DPI flagged your traffic as “high bandwidth.”
Governments: Turning Surveillance Into Policy
Governments, especially in countries with strict internet laws, rely on DPI to censor content and monitor citizens. China’s Great Firewall is one of the most famous examples, using DPI to detect and block VPN connections, encrypted messaging apps, or politically sensitive content.
Companies: Killing Your YouTube Breaks
Then there are corporations. Large enterprises use DPI to enforce internal security and productivity policies, blocking things like YouTube, game servers, or cloud storage tools they consider a risk or a distraction.
Schools and Libraries: Silently Controlling What You See
And yes, even schools, colleges, and libraries get in on it. DPI can stop students from accessing certain apps, social media platforms, or even VPN websites. It’s all about control, and DPI hands them the toolkit.
“Nothing to Hide”? DPI Might Disagree
So, when people say, “I have nothing to hide,” they might not realize how far DPI can go, not just reading traffic, but judging and reshaping it too.
How Deep Packet Inspection Actually Works (No Jargon Needed)
You don’t need a degree in networking to understand the basics of how deep packet inspection actually works. Think of it like airport security, but for every single data packet your device sends or receives.

Think of DPI Like Airport Security for Data
Step 1: You Send a Request, Innocent Enough
Maybe you're loading a website, watching a video, or checking your email, whatever it is, your device sends out a data request.
Step 2: Routers Peek at the Surface Info
Your data travels through standard routers, which read the header information, things like IP addresses, ports, and protocol type (HTTP, HTTPS, etc.).
Step 3: DPI Digs Into the Payload
This is where deep packet inspection steps in. It doesn’t just look at where your traffic is going, it digs into the actual content inside each packet, known as the payload.
Step 4: Filters Decide What Gets Through
If the content matches certain signatures, say, a torrent client, gaming service, or VPN handshake, it might be flagged, throttled, blocked, or even logged.
Why You Probably Won’t Notice It Happening
So instead of just saying, “This packet is headed to YouTube,” DPI might also say, “It contains HD video data, let’s slow it down.”
It’s subtle, it’s fast, and unless you’re specifically measuring your network behavior, you probably won’t notice it’s happening. But if your streams buffer more when using a VPN, or your downloads stall without reason, DPI might be working behind the scenes.
Why Deep Packet Inspection Is a Big Privacy Problem
Here’s the uncomfortable truth: deep packet inspection doesn’t just slow down your internet. It messes with your privacy on a fundamental level.

They’re Not Just Watching, They’re Interpreting Your Intent
Imagine someone standing over your shoulder, not only watching what websites you visit but trying to guess why you’re visiting them.
That’s the kind of power DPI puts into the hands of whoever controls the network.
Your Online Life, Open for Inspection
At its core, DPI allows third parties, whether that’s an ISP, a corporate firewall, or a government agency, to read, analyze, and act based on your internet activity.
And we’re not just talking about where your traffic is headed. It’s the payload, the actual emails, chats, streams, and searches, that gets exposed.
Even Encryption Can Be Flagged
It doesn’t stop there. DPI can disrupt or block encryption, breaking tunnels like SSL or VPNs.
Some systems even hunt for VPN connections and shut them down, not because they’re dangerous, but because they’re unreadable.
Net Neutrality? DPI Throws That Out the Window
This kind of filtering undermines net neutrality and shatters the idea of equal access. Your traffic isn’t just being routed, it’s being judged.
And if encryption itself starts to raise red flags, what else is left to protect your privacy?
How VPNs Outsmart Deep Packet Inspection (When They’re Built Right)
Now for some good news: VPNs were practically made to fight back against deep packet inspection and they’re surprisingly effective at it, if you know what to look for.

The Encrypted Tunnel That Hides What You Do
A VPN creates a secure, encrypted tunnel between your device and the internet. Everything inside that tunnel, your data packets, browsing activity and app usage, is hidden from plain view.
DPI systems can’t easily read it, making classification and content filtering much harder.
But Metadata Still Leaks Clues
But here’s where things get tricky. Even if DPI can’t read the actual data, it might still spot patterns, like packet size, frequency, or unusual ports, that hint you’re using a VPN.
That metadata can be enough to get your connection flagged, throttled, or even blocked in restrictive regions.
Stealth Tech Helps You Blend Into the Background
This is where obfuscation comes in, not to re-encrypt your data, but to disguise the traffic patterns themselves. Tools like Stunnel, XOR scrambling, and Obfsproxy make your VPN traffic blend in with regular web browsing.
So while no solution is foolproof, stealth-enabled VPNs go beyond encryption to camouflage your activity entirely, making it much harder for DPI to even know you’re using a VPN at all.
The VPN Features That Actually Beat DPI (And When to Use Them)
Let’s talk tools. If you live somewhere with aggressive censorship, or if you’re just sick of slow speeds during a video call, you’ll need more than basic encryption. You need a VPN that’s purpose-built to bypass deep packet inspection.

DPI-Resistant Features That Actually Work
Obfuscated Servers: Great for Everyday Bypassing
These are ideal for users in moderately restricted environments. Obfuscated servers make your VPN traffic look ordinary, great for getting around firewalls without raising suspicion.→ Example: NordVPN’s Obfuscated Servers
Stealth Modes: For Places Where VPNs Are Targeted
If VPNs are banned or blocked outright, stealth modes like Obfsproxy, Stunnel, XOR, and Shadowsocks are your best bet. They’re built for high-censorship zones like China or Iran, where DPI looks for and actively disrupts encrypted tunnels.→ Example: Surfshark’s NoBorders mode, ExpressVPN’s Stealth servers
WireGuard + Custom Ports: Speed With Subtlety
For users looking to maintain speed and security while avoiding detection, using WireGuard with non-standard ports is smart. It’s fast, but customizing ports helps prevent DPI from flagging your connection.
Split Tunneling: Just Encrypt What You Need To
This one’s less about censorship and more about staying under the radar on school, work, or shared networks. Route only sensitive apps through the VPN to reduce the volume of encrypted traffic and avoid triggering filters.
Not All VPNs Can Handle DPI, Choose Carefully
Not every provider is up to the task. If a VPN doesn’t mention bypassing DPI, stealth tech, or anti-censorship features, it likely won’t hold up in tough environments.
Look for providers that openly discuss how they counter DPI and offer frequent server refreshes and protocol options.
The Catch: Even VPNs Have Limits Against DPI
As powerful as VPNs can be, they’re not invincible. Especially when deep packet inspection is backed by serious resources, think authoritarian governments, major telecoms, or enterprise-grade firewalls.
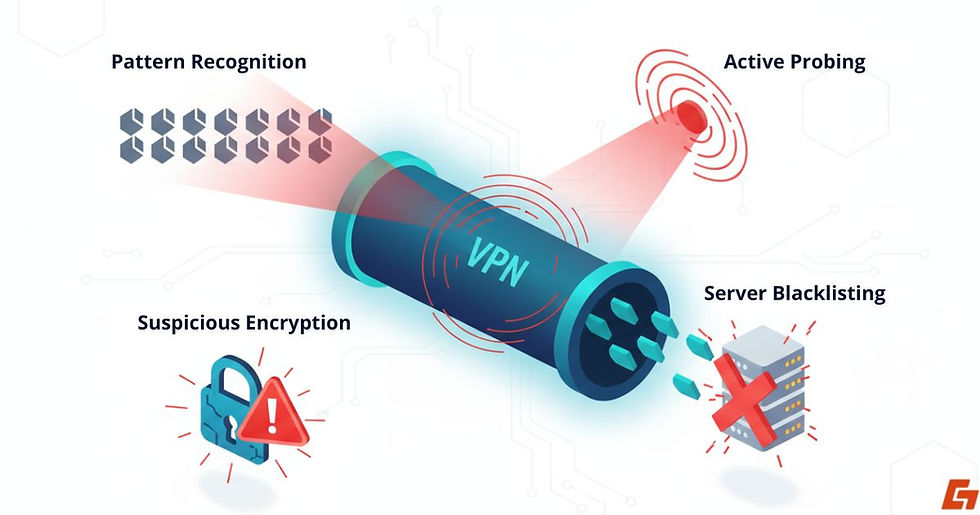
DPI Doesn’t Need to Read, Just Recognize Patterns
Some DPI systems are trained to recognize VPN traffic based on telltale signs. They don’t need to read the content, just spotting repeated packet sizes, odd port choices, or timing anomalies is sometimes enough.
If your VPN doesn’t use obfuscation or mimic regular traffic patterns, it may still get flagged.
Encrypted = Suspicious in Some Countries
In some countries, encrypted traffic itself can look suspicious. So even if your VPN is technically working, the mere fact that it hides your data can raise red flags.
Governments Can Still Shut It Down
Even more aggressive? Some governments blacklist VPN server IPs or use active probing, a technique where they send fake requests to detect and expose VPN endpoints.
This isn’t theory, it’s happening in places like China, Iran, and Russia. And depending on local laws, using a VPN could have legal or political consequences.
It’s a Tech Arms Race and You Need a VPN That Keeps Up
The fight between VPNs and DPI is ongoing. Every time a provider builds a better stealth protocol, DPI vendors adapt with sharper detection tools.
That’s why choosing a VPN that updates regularly, rotates servers, and offers multiple bypass features isn’t just a bonus, it’s survival.
What DPI Looks Like in the Real World (And Why It Should Worry You)
Let’s stop theorizing and look at how deep packet inspection plays out in the wild. These real-world cases show just how much control DPI gives and why VPNs are often the only line of defense.

China’s Great Firewall: The Gold Standard of Censorship
Probably the most infamous use of DPI on the planet. China’s censorship system uses advanced DPI techniques to block not just websites, but also VPN protocols, Tor traffic, and encrypted DNS.
Most VPNs simply don’t work here, unless they include heavy-duty obfuscation like Shadowsocks, stealth servers, or other custom bypass modes.
Iran’s Throttling Playbook During Unrest
During political protests, Iranian authorities don’t always shut down the internet entirely, they selectively slow it down. DPI is used to detect and throttle VPN traffic, encrypted chat apps, and even file sync services like cloud backups.
Locals often turn to community-built tools or under-the-radar VPN providers just to stay connected.
India’s ISP Blocks: Sometimes It’s Politics, Sometimes It’s Bandwidth
In India, several ISPs have been caught throttling P2P traffic and blocking VPN usage, especially during elections or periods of unrest.
While the motivation isn't always censorship, DPI is used to enforce government mandates or simply reduce network load.
Corporate Firewalls: The Censorship You Didn’t Notice
You don’t need to be in a repressive country to feel DPI’s effects. Offices, schools, and libraries routinely use DPI to block gaming, streaming, or even secure messaging apps.
Ever wonder why WhatsApp Web or Discord won’t load on school Wi-Fi? It’s probably not a glitch, it’s DPI doing what it was designed to do.
You Can’t Outsmart DPI Unless You Understand It First
These examples show just how versatile and invasive, deep packet inspection really is. But they also highlight why VPNs with strong anti-DPI features matter.
Whether you’re up against a government firewall or just trying to stream Netflix during lunch break, understanding DPI is the first step toward outsmarting it.
Control Your Traffic, Or Let Someone Else Decide
We’ve broken down how deep packet inspection works, who’s using it, and how VPNs step in to protect your privacy when the network starts watching too closely. From censorship to throttling, DPI isn’t just technical, it’s personal.
The takeaway? If someone else controls what your internet traffic looks like, they can shape what you see and what you don’t. A reliable, well-equipped VPN isn’t just a convenience anymore; it’s a line of defense.
So, are you browsing freely, or just following the rules someone else quietly set for you?



Comments